- Published on
Magento 1 BL/CustomGrid Security Flaw
- Authors
- Name
- Niko Granö
- Github
- @NikoGrano
- Socials
- Address
Mail
P.O. Box 5
FI-01711 VANTAA
FINLAND- Company details
Other
VAT Registered
FI29067989

As most of people can notice, I have been going trough Magento modules lately hunting for possible security flaws. This time I decided to review BL/CustomGrid, why? This module is not maintained for long time and it is used widely in many Magento 1 shops. Let’s see what problems we were able to find.
Discovering the Flaw
I saw post here and I noticed BL/CustomGrid to be on list, however it’s unmaintained and there seems to be no fix. So to fix it I had to go trough this module and check what is wrong with it.
Object Injection
Classic CWE-502. This means in PHP usually, we are receiving input and using unserialize to parse it. This allows attacker to execute code inside the Magento install. You can check more here.
Problem happens in the controllers. There we are doing following.
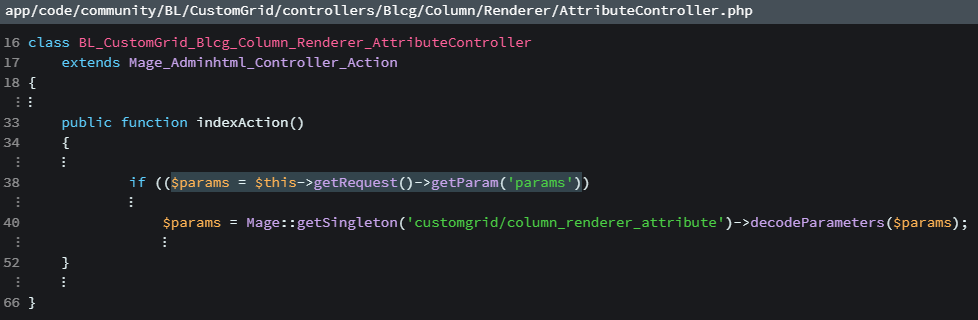
On line 38 we are receiving user input and then we are using method decodeParamters to decode input. This looks fine so far, however, the problem is not in the controller. The problem is in the method, so let’s check this method.
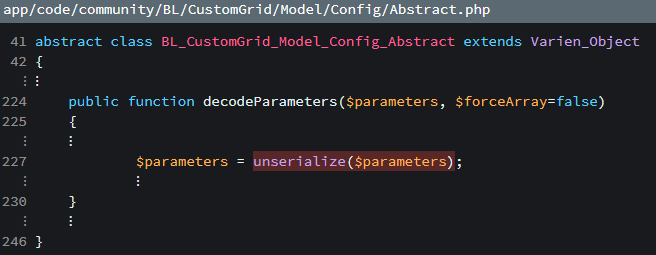
This is just one of examples. This variable is made based on user input. In any cases, where user input is injected into the site code, it should be escaped.
Overall
The code is poorly made and it includes many security issues by default. Even the original author have abounded this module and provides no longer updates. The Magento store page for this module have been remove and only way to find sources for this module is trough Github.
My recommendation is to migrate to something similar maintained alternative, instead of using this one.
Fixing this module
Fix for this module is currently available here. Upgrade is strongly recommended.
I have still decided to fix this module. I’m currently working the fix and I will be publishing it on the GitHub as soon as I can.
I will be updating here link to the safe version of this module later.